Read Very Easiest Method to Read Whatsapp messages using Database.db.crypt12 File on Android Without Key Require, In short Form Hack Whatsapp chat of anybody by Transferring Their Database Crypt12 File to your Android Smartphone. Both Decrypt & Hack Chat Method is Same, Because When you Decrypt Encrypted Database File, you will see their all Past Chat messages in Whatsapp app.
- How Do I View A .db File
- How To View .db File Online
- Read Whatsapp Db File Online
- How To Open .db Whatsapp File
To Decrypt Whatsapp messages by Database .db.crypt12 File, Just you will need only their Saved Messages Database File which Extension is .db.crypt12 then You Can read their all Sent & Received Messages by Extracting it. This is not the only one Way to hack Chat , We also Shared Many tricks by Which you Can Hack Whatsapp account online by Spy apps & How to Hack Using Whatsapp Web Option.
Many online Sites Claims they Will Hack Whatsapp Messages by entering Mobile Number but its Not Possible Because this Messenger app Uses End to End Encrypt Security by Which only the Person who Send or Received Can View This Messages but Nothing is impossible ,We can access other messages with their presence and things because Whatsapp Stores this Chat Messages in One file which we Will Hack in this article.
Update :- New Methods added
Post Contents
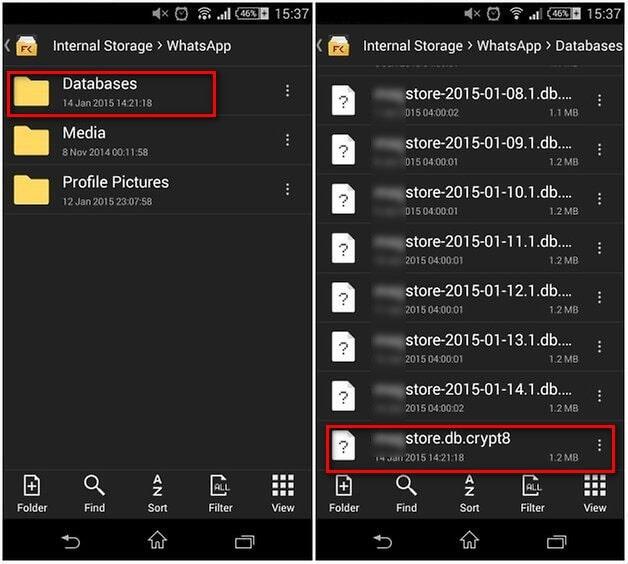
Go to the File Manager app Device Storage (Internal Storage) WhatsApp folder Databases or SD Card folder. Then go to the WhatsApp folder Databases folder. Check where the backup file is saved according to the file name. The file name contains the date of the backup. The saved files will be available in “msgstore-YYYY-MM-DD.1.db” format. Steps to open the database and display your conversations. Download the GitHub project by clicking on the 'Clone or download' green button 'Download ZIP'. In the extracted folder, double-click on 'whatsapp.html'. Click on the 'Chose a file' button and select the 'ChatStorage.sqlite' file extracted from your backup. If there is no prompt, uninstall Whatsapp and reinstall Whatsapp, making sure that the chat you want to restore is named “msgstore.db.crypt12” and saved on your phone in “WhatsApp/Databases.
- 1 How to Convert Whatsapp database .db.crypt12 into Text
How to Convert Whatsapp database .db.crypt12 into Text
This is the Very Simple Method But Chance to Whatsapp Database Decrypt is Very Less, If its Works for you then enjoy Otherwise try Below Shared 100% Working Methods.
- First of all , Take Victim’s mobile.
- Open File Manger & Navigate to SD Card >> Whatsapp Folder.
- Now Copy this Folder & Paste it in Your Sd card. (if you already Using Your Whatsapp Account in Your Phone then Firstly Move Your Whatsapp Folder to Other Folder)
- Now Goto Settings >> Apps >> Whatsapp , Hit on Clear Data & Cache.
- Open Whatsapp & Restore it.
- Within Few Minutes , All the messages Will be restored.
- This are the Steps to Decrypt Whatsapp Databases File or Hack Chat Messages.
How to View Whatsapp Database on android without keys (2020)
- First of All Copy the Database File From Phone/sd Card : Whatsapp/Databases/msgstore.db.crypt
- Now Download the Omni crypt app
- If the Crypt File is Below Version 6 then You Don’t Need to Root your Device otherwise key can be find on Rooted Device
- Now Open the App and Select Your Database file to Decrypt it
- Once it Decrypted , Now we have to Convert it to Human Readable form
- Open Whatscrypt.com and upload your Decrypted file
- Click on Process / Download Zip Button
- Extract the Zip and Read the Decrypt Whatsapp Message Easily
- You can also Recrypt the File by adding your Message in it.
In the above Method You Can view Only Past Message , You will not get any real Time Updates & Future messages. If You wants to Get real Time Updates Then You have to Change your mac address by their Address & Verify it By otp then You Can both run One Whatsapp Account , Get Explanation of This Method.
How Whatsapp Decryption works ?
Whatsapp Takes Daily backup of Our Chat & Save this Messages in the .db.crypt12 Extension File which saves in SD Card or In Phone Memory. When We Replace this File in our Whatsapp Folder then it Shows that File Messages. Sometime keys Required Which Stored in Data/data/Com.whatsapp/Files/ If your device is Rooted then it can easily access it.
How to View / Hack Chat Messages by Whatsapp Web (Real time)
Just open Whatsapp Web ( https://web.whatsapp.com ) in your Pc/Laptop or Use parallel Space app for Mobile, Now Scan Qr code in Victim’s Mobile. Done ! Now Don’t Clear Cookies of Browser & Read their Messages in Real Time Even you can also Read their Past Messages.
You know In recent Version , You will also get Pop up to Save back up on Google Drive. If your Victim Turn on this Option then You Can Copy this File From Their Google Drive also but you have to Access their Google Account for this.
Tags :- how to Decrypt Whatsapp Messages by Database .db.crypt12 File , hack whatsapp chat messages online by whatsapp web
WhatsApp backup conversation files are now saved with the .crypt12 extension. From crypt9, they seem to be using a modified version of Spongy Castle – a cryptography API library for Android.
All the findings below are based on reverse engineering work done on WhatCrypt and Omni-Crypt. I would like to highlight that IGLogger proved to be a very useful tool when it came to smali code debugging.
Extract Key File
To decrypt the crypt12 files, you will first need the key file. The key file stores the encryption key, K. WhatsApp stores the key file in a secure location: /data/data/com.whatsapp/files/key.
If your phone is rooted, extracting this file is easy. I will not go through the steps again, as it’s already mentioned in the crypt8 decryption article. If your phone is not rooted, refer to instructions from WhatCrypt and Omni-Crypt for details on extracting the key file. The idea is to install an older version of WhatsApp, where Android ADB backup was still working and extract the key file from the backup.
Extract crypt12 Backup File
Pull the encrypted WhatsApp messages file from your phone using ADB.
Decryption Keys
This section is just for your information and you can skip this section.
The encryption method being used is AES with a key (K) length of 256 bits and an initialisation vector (IV) size of 128 bits. The 256-bit AES key is saved from offset 0x7E till 0x9D in the file. Offsets start from 0x00. You can extract the AES key with hexdump and assign the value to variable $k.
The $k variable will hold a 64-digit hexadecimal value in ASCII that is actually 256 bits in length.
The IV or the initialisation vector is saved from offset 0x33 till 0x42 in the crypt12 file. The IV value will be different for every crypt12 file.
The K and IV extraction method is similar to what we have done for crypt8 files before.
Strip Header / Footer in crypt12 File
Again, this section is just for your information and you can skip this section.
Before we start the decryption process, we will need to strip the 67 byte header and 20 byte footer from the crypt12 file.
The above dd command will strip the the first 67 bytes from the crypt12 file and save it to a file with extension crypt12.enc. The truncate command will strip the last 20 bytes from the crypt12 file.
Decrypt crypt12 File
As the WhatsApp AES cryptography API library seems to be a modified version, we will no longer be able to use openssl to decrypt the crypt12 file. I have yet to determine what has been modified.
To decrypt crypt12 files, I have written a simple Java program that will use the modified cryptography API library instead. For the cryptography API library, I have extracted the modified Spongy Castle cryptography class files from the Omni-Crypt APK file using dex2jar. You can find the Java program and crypto library over here at GitLab.
The Java program will create 3 output files:
msgstore.db.crypt12.enc– encrypted file with header and footer stripped.msgstore.db.zlib– decrypted file in zlib format.msgstore.db– decrypted sqlite3 database file.

How Do I View A .db File
Below is how you can compile and run the Java program.

How To View .db File Online
Final Words
To use the Java decryption tool, you will need to use OpenJDK. Oracle require JCE Provider libraries to be signed. OpenJDK does not have this requirement. If you try running the Java program on Oracle JDK, you will most likely get the following exception.
There are some workarounds to bypass the error, but it has not worked for me so far.
Read Whatsapp Db File Online
Decryption failed when using the modified cryptography API library from WhatsApp and WhatCrypt. Only Omni-Crypt library is working. I have yet to determine the reason for this. If you have any further information on this, leave a comment.
Mohamed Ibrahim
How To Open .db Whatsapp File
ibrahim = { interested_in(unix, linux, android, open_source, reverse_engineering); coding(c, shell, php, python, java, javascript, nodejs, react); plays_on(xbox, ps4); linux_desktop_user(true); }